Late yesterday evening, we were notified by the Australian Cyber Security Centre about the prevalence of a particular variant of malware called Emotet that is targeting Australian businesses and individuals.
This variant tricks people into opening an attachment, generally Word or PDF, or downloading a document via a web link that has malicious software embedded into the document. Once someone falls victim to this, it then accesses your address book in your email and forwards copies of the malicious email to everyone in the address book.
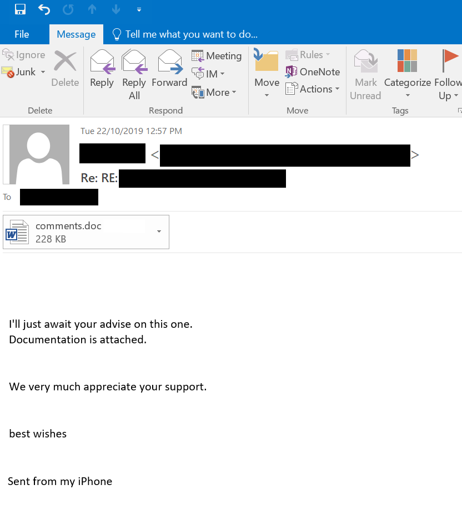
The below is a sample of one email that has been seen in the wild;
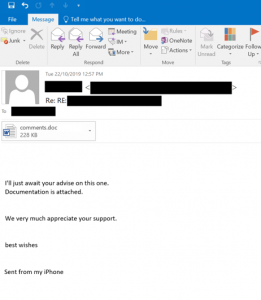
It will also search your systems for other systems it can infect with malicious software such as ransomware. Naturally, this is not something you want to happen and could be devastating to your firm if infected.
So how can you stay safe?
- Ensure your systems are patched and up to date; if you’re a managed services client, we take care of this for you.
- Switch off support for Macro’s in Microsoft Office or only allow trusted Macros to run.
- Engage Cyber Security Awareness Training for you and your staff, talk to us to find out more.
- Have a next generation firewall that’s configured correctly and receiving up to date threat information. Those clients that have purchased firewalls from us already talk to us about updating settings to help stop known bad sites.
- Ensure your systems are backed up and stored offsite, preferably in the “cloud”, and that they are only accessible by those that need access to them.
- Ultimately, you want to have an in-depth defence strategy with your protections and ensure there are multiple layers in place, like a castle. We are happy to provide a third-party assessment of your system to give you peace of mind that your defences are adequate.
Call us today on 08 6244 2556 to learn how you can protect yourself from the ever-increasing risks of infection or submit the form at the top of the page.





 Contact Us On
Contact Us On



